证书修复
文章目录
- 证书修复
- 基础知识
- Truncated 1
- Truncated 2
- Jumbled
基础知识
- 为什么要引入证书?
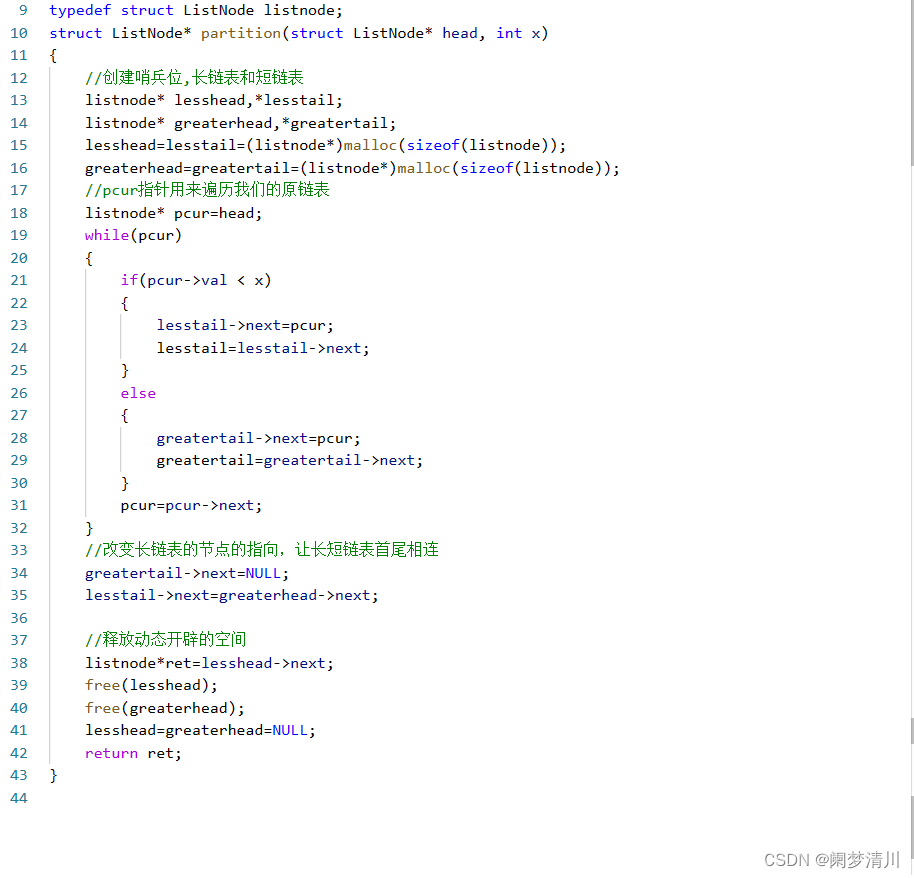
在正常题目中,大部分直接给出了数字,但是数字在现实世界中传输不稳定,容易在某处出现错误,所以我们将所有的数字信息使用统一的格式进行封装,封装后的内容称为证书
- 分类?
常见的有两种格式,一种是PEM,一种是DER,最终都可以转化为数字,之间都可以进行转换
- 工具?
openssl
参考:https://blog.csdn.net/zyhse/article/details/108186278
- 手撕?
私钥:
-----BEGIN RSA PRIVATE KEY----- MIICXQIBAAKBgQCg0VTVv5fED3eXtEgZ0Jxgj6S1w45w2DvBMmcTjG7/TBqs7+Pd tXHhtB2RHHq2E2z5BJMYlWNFDh9CcMq7xCB8VMTae4SiAxHPu6voK5/mC99IoI1X g50M35Rk2EJivMBrwwgJWmmH9grQfWaaMStafkEzITeI7s8lhjJIuRNJ7wIDAQAB AoGAD4JwxJaQO/Pj7EkSRQ8V7cgcsfz0sVRhWu4R+9Qo5k1AK1qNZtX3cDWPPm35 NbMk6NU0nIPXyZKlmCJJoxc0rLHbGcTI2CkmdRS8Hve7++JC1DUPZ6ACpW0z5W0a lK3HHGjwINw5q30AZMERsWTia6BpjclKA839UW/9lm6HeUkCQQDKl+ScBYI3+W6Z EYzjg/kZEsuhFj3pI2GB/3VO8+8aJg+sjS2a7oZtUai2g2mDsFz4UOeGKJtoWZJb yGlfxnxHAkEAyzYwqv/8spYH8IM9x/BcFD7pL63+l12kz2cZ5xImvuclYuhjEyii XXNRUHqNQ8EpWrbqJCtgoosQkjOpg/QhGQJAG0oypUGotNmIqF3Q2KTiXRpHC7/v PwRhEh3TM3twbdlKqzepOQGAYiFp1IwHHpIXM+vSBCRcKsZGDM8GQrx96QJBAI2f RKfII+qqWPor3SC8yM9rUMRj9Ky1HKlW51x87/fXy9x0rKeriAys05zM7CquMg4A sIlomb5uQKxDyP4nY/ECQQDGfKbZiPU6vqghWUMaFGUSqNlCl41Kj4Py1CbxCV47 8bW5uLHMu60qMcZAGIBEekX14HkCaQYawTtfaPF3fX8H -----END RSA PRIVATE KEY-----其内容都是由base64编码生成,想要手撕,就要先将其转化为十六进制
两种转化方法
- 在文件中读
with open('./priv.pem', 'r') as f:data = f.read()key_64 = ''.join(data.split('\n')[1:-1]) key_num = libnum.s2n(base64.b64decode(key_64)) key_hex = hex(key_num)[2:] print(key_hex)''' 3082025d02010002818100a0d154d5bf97c40f7797b44819d09c608fa4b5c38e70d83bc13267138c6eff4c1aacefe3ddb571e1b41d911c7ab6136cf90493189563450e1f4270cabbc4207c54c4da7b84a20311cfbbabe82b9fe60bdf48a08d57839d0cdf9464d84262bcc06bc308095a6987f60ad07d669a312b5a7e4133213788eecf25863248b91349ef02030100010281800f8270c496903bf3e3ec4912450f15edc81cb1fcf4b154615aee11fbd428e64d402b5a8d66d5f770358f3e6df935b324e8d5349c83d7c992a5982249a31734acb1db19c4c8d829267514bc1ef7bbfbe242d4350f67a002a56d33e56d1a94adc71c68f020dc39ab7d0064c111b164e26ba0698dc94a03cdfd516ffd966e877949024100ca97e49c058237f96e99118ce383f91912cba1163de9236181ff754ef3ef1a260fac8d2d9aee866d51a8b6836983b05cf850e786289b6859925bc8695fc67c47024100cb3630aafffcb29607f0833dc7f05c143ee92fadfe975da4cf6719e71226bee72562e8631328a25d7351507a8d43c1295ab6ea242b60a28b109233a983f4211902401b4a32a541a8b4d988a85dd0d8a4e25d1a470bbfef3f0461121dd3337b706dd94aab37a9390180622169d48c071e921733ebd204245c2ac6460ccf0642bc7de90241008d9f44a7c823eaaa58fa2bdd20bcc8cf6b50c463f4acb51ca956e75c7ceff7d7cbdc74aca7ab880cacd39cccec2aae320e00b0896899be6e40ac43c8fe2763f1024100c67ca6d988f53abea82159431a146512a8d942978d4a8f83f2d426f1095e3bf1b5b9b8b1ccbbad2a31c6401880447a45f5e0790269061ac13b5f68f1777d7f07 '''
- 直接输入
from base64 import b64decode import binasciis = '''MIICXQIBAAKBgQCg0VTVv5fED3eXtEgZ0Jxgj6S1w45w2DvBMmcTjG7/TBqs7+Pd tXHhtB2RHHq2E2z5BJMYlWNFDh9CcMq7xCB8VMTae4SiAxHPu6voK5/mC99IoI1X g50M35Rk2EJivMBrwwgJWmmH9grQfWaaMStafkEzITeI7s8lhjJIuRNJ7wIDAQAB AoGAD4JwxJaQO/Pj7EkSRQ8V7cgcsfz0sVRhWu4R+9Qo5k1AK1qNZtX3cDWPPm35 NbMk6NU0nIPXyZKlmCJJoxc0rLHbGcTI2CkmdRS8Hve7++JC1DUPZ6ACpW0z5W0a lK3HHGjwINw5q30AZMERsWTia6BpjclKA839UW/9lm6HeUkCQQDKl+ScBYI3+W6Z EYzjg/kZEsuhFj3pI2GB/3VO8+8aJg+sjS2a7oZtUai2g2mDsFz4UOeGKJtoWZJb yGlfxnxHAkEAyzYwqv/8spYH8IM9x/BcFD7pL63+l12kz2cZ5xImvuclYuhjEyii XXNRUHqNQ8EpWrbqJCtgoosQkjOpg/QhGQJAG0oypUGotNmIqF3Q2KTiXRpHC7/v PwRhEh3TM3twbdlKqzepOQGAYiFp1IwHHpIXM+vSBCRcKsZGDM8GQrx96QJBAI2f RKfII+qqWPor3SC8yM9rUMRj9Ky1HKlW51x87/fXy9x0rKeriAys05zM7CquMg4A sIlomb5uQKxDyP4nY/ECQQDGfKbZiPU6vqghWUMaFGUSqNlCl41Kj4Py1CbxCV47 8bW5uLHMu60qMcZAGIBEekX14HkCaQYawTtfaPF3fX8H'''s = b64decode(s)print(binascii.hexlify(s))''' 3082025d02010002818100a0d154d5bf97c40f7797b44819d09c608fa4b5c38e70d83bc13267138c6eff4c1aacefe3ddb571e1b41d911c7ab6136cf90493189563450e1f4270cabbc4207c54c4da7b84a20311cfbbabe82b9fe60bdf48a08d57839d0cdf9464d84262bcc06bc308095a6987f60ad07d669a312b5a7e4133213788eecf25863248b91349ef02030100010281800f8270c496903bf3e3ec4912450f15edc81cb1fcf4b154615aee11fbd428e64d402b5a8d66d5f770358f3e6df935b324e8d5349c83d7c992a5982249a31734acb1db19c4c8d829267514bc1ef7bbfbe242d4350f67a002a56d33e56d1a94adc71c68f020dc39ab7d0064c111b164e26ba0698dc94a03cdfd516ffd966e877949024100ca97e49c058237f96e99118ce383f91912cba1163de9236181ff754ef3ef1a260fac8d2d9aee866d51a8b6836983b05cf850e786289b6859925bc8695fc67c47024100cb3630aafffcb29607f0833dc7f05c143ee92fadfe975da4cf6719e71226bee72562e8631328a25d7351507a8d43c1295ab6ea242b60a28b109233a983f4211902401b4a32a541a8b4d988a85dd0d8a4e25d1a470bbfef3f0461121dd3337b706dd94aab37a9390180622169d48c071e921733ebd204245c2ac6460ccf0642bc7de90241008d9f44a7c823eaaa58fa2bdd20bcc8cf6b50c463f4acb51ca956e75c7ceff7d7cbdc74aca7ab880cacd39cccec2aae320e00b0896899be6e40ac43c8fe2763f1024100c67ca6d988f53abea82159431a146512a8d942978d4a8f83f2d426f1095e3bf1b5b9b8b1ccbbad2a31c6401880447a45f5e0790269061ac13b5f68f1777d7f07 '''证书中存储的顺序
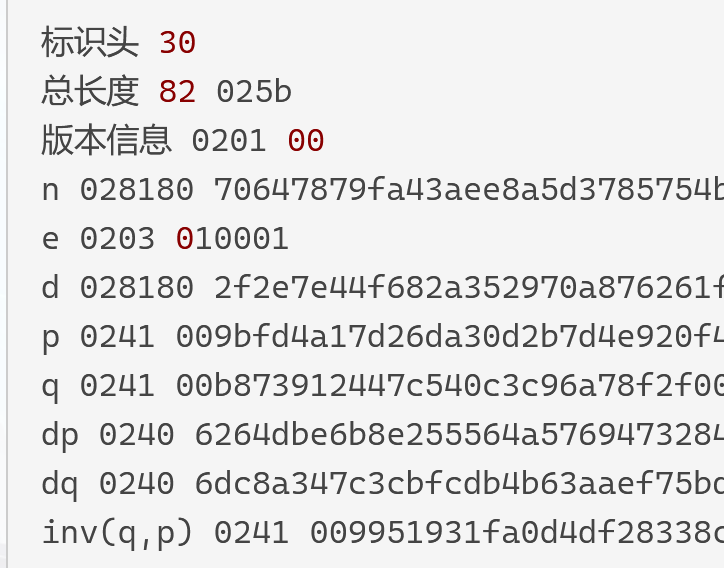
RSAPrivateKey ::= SEQUENCE {version Version, 0表示两个素数的RSA 1表示多素数的RSAmodulus INTEGER, -- npublicExponent INTEGER, -- eprivateExponent INTEGER, -- dprime1 INTEGER, -- pprime2 INTEGER, -- qexponent1 INTEGER, -- d mod (p-1)exponent2 INTEGER, -- d mod (q-1)coefficient INTEGER, -- (inverse of q) mod potherPrimeInfos OtherPrimeInfos OPTIONAL }对应16进制 以上面的为例 格式:tag +
3082025d #30 是Sequence的tag 结构开始 82表示接下来两个bytes是这个Sequence的长度双字节长度 即0x025d个bytes020100 #02 是整数的tag 01表示这个整数占1byte 00表示值value为0x00 = 0 即两个素数的RSA028181 #02 整数tag 中间的81表示长度类型 代表后面一个跟着一个单字节长度 最后的81代表长度为0x81 00a0d154d5bf97c40f7797b44819d09c608fa4b5c38e70d83bc13267138c6eff4c1aacefe3ddb571e1b41d911c7ab6136cf90493189563450e1f4270cabbc4207c54c4da7b84a20311cfbbabe82b9fe60bdf48a08d57839d0cdf9464d84262bcc06bc308095a6987f60ad07d669a312b5a7e4133213788eecf25863248b91349ef0203 #02 整数tag 0x03表示长度 010001028180 0f8270c496903bf3e3ec4912450f15edc81cb1fcf4b154615aee11fbd428e64d402b5a8d66d5f770358f3e6df935b324e8d5349c83d7c992a5982249a31734acb1db19c4c8d829267514bc1ef7bbfbe242d4350f67a002a56d33e56d1a94adc71c68f020dc39ab7d0064c111b164e26ba0698dc94a03cdfd516ffd966e877949024100ca97e49c058237f96e99118ce383f91912cba1163de9236181ff754ef3ef1a260fac8d2d9aee866d51a8b6836983b05cf850e786289b6859925bc8695fc67c47024100cb3630aafffcb29607f0833dc7f05c143ee92fadfe975da4cf6719e71226bee72562e8631328a25d7351507a8d43c1295ab6ea242b60a28b109233a983f4211902401b4a32a541a8b4d988a85dd0d8a4e25d1a470bbfef3f0461121dd3337b706dd94aab37a9390180622169d48c071e921733ebd204245c2ac6460ccf0642bc7de90241008d9f44a7c823eaaa58fa2bdd20bcc8cf6b50c463f4acb51ca956e75c7ceff7d7cbdc74aca7ab880cacd39cccec2aae320e00b0896899be6e40ac43c8fe2763f1024100c67ca6d988f53abea82159431a146512a8d942978d4a8f83f2d426f1095e3bf1b5b9b8b1ccbbad2a31c6401880447a45f5e0790269061ac13b5f68f1777d7f07
学习参考及附件来源:
https://tangcuxiaojikuai.xyz/post/e1a814d3.html#more
https://www.cnblogs.com/mumuhhh/p/18122781
https://github.com/tamuctf/tamuctf-2024/blob/master/crypto
下面的题目复现是基于鸡块师傅和mumu师傅的博客展开学习,收益颇丰!先给大师傅磕一个
Truncated 1
题目描述
Only part of the private key was able to be retrieved. Decrypt the flag.txt.enc file.
flag.txt.enc
直接在文件中读吧 粘贴也是乱码
private.pem
ZXPI0zfM5EJkeooRvNr3RKQEoQKBgQD0WrYbxhBveSRYvkOV0+omfutwS6wIoCme
CYCq5MboHdZn8NDCHy+Y66b+G/GMZJewqEKQSLwHcAjKHxouneFXp6AxV0rkBWtO
RNnjXfthsWXvOgBJzGm8CJQS+xVtUpYc4l1QnYaQpc0/SClSTPG775H5DnJ8t4rK
oNQur+/pcwKBgD1BU0AjW6x+GYPXUzA0/tXQpu5XaAMxkinhiiOJWT/AExzJU8Jt
eQULJ3EDENG6acSuwMhm0WMLhQ0JG6gIejRyOBZSIqjESWGHPmkU1XbUDz0iLb1h
HTqJMAWYKWJs4RnJbx6NGJAhd2Ni4CyOGmujYpqNnp1qfZNhmcj/VOeBAoGBAJgD
stU2c9UVlTIMM7mLG1kVjlzPBtha42ko2j32k3Ol1FPXcdfCVPcaa0ockjnX/rJt
CvP9+9PYs+8iSESF/cFtS/BGMRYH9Qi9NpwHRLMzDIo2GCXRIFpVL+FbCKp5PV/8
xza2uRdVvolG2EYWDjDvym0Zusmx2YtTYI0m8ObXAoGAZ6T8aF6GAZ0s814ZfEcy
zZGrZZQ/MJ7W8ZGdU1/y+204LzfGsW+d+sTPfQPYhn03/qU3SFhP095sYzELeOOZ
3yITOftHEdMP3XffnAudgn3tBHrtu0EsVFL44H7CWe4hx3M49M0lfERD60lPwUG1
8hY5qcthSko1f1WkTgN7Rrs=
-----END PRIVATE KEY-----
public.pem
-----BEGIN PUBLIC KEY-----
MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEA64u2qOSKwRf6GWPrq9ZX
uWqvooTq2uz/3obioiWMY2l2tLpi2Jgiq7F40t9QHLuIzcggU6bRH5Cn2gsh1DtE
UQYLMkszbp88akQqpPEa7t6leIqnT8Z4rFqj6sRpdYSQS8U2FzAzWDRvhY4oEliw
comX84WCVh8BKe38qOqN1QvhZVBY00JoUk2x/HBFNCA8VpEZIeTSKvH0Rc/Dzy5h
KoHBRaL8bBLYjhqO2PNfAkvHewJIqRyqtXXbedqqDn6vp9JX4lVcS5n/i95kQN98
JYn2RSuhTxk+v1ZHpEiSLImzc+9aOAPPtsikZPsah6JOnjDbhctfZGRn1MfFfzOd
UwIDAQAB
-----END PUBLIC KEY-----
解题:
首先是不完整的私钥文件,前半部分是丢失了,但是不影响我们提取后面的数据,所以,先进行base64解码,然后转化成hex16机制,根据数据的特征提取数据
exp:
from base64 import b64decode
import binasciis = '''ZXPI0zfM5EJkeooRvNr3RKQEoQKBgQD0WrYbxhBveSRYvkOV0+omfutwS6wIoCme
CYCq5MboHdZn8NDCHy+Y66b+G/GMZJewqEKQSLwHcAjKHxouneFXp6AxV0rkBWtO
RNnjXfthsWXvOgBJzGm8CJQS+xVtUpYc4l1QnYaQpc0/SClSTPG775H5DnJ8t4rK
oNQur+/pcwKBgD1BU0AjW6x+GYPXUzA0/tXQpu5XaAMxkinhiiOJWT/AExzJU8Jt
eQULJ3EDENG6acSuwMhm0WMLhQ0JG6gIejRyOBZSIqjESWGHPmkU1XbUDz0iLb1h
HTqJMAWYKWJs4RnJbx6NGJAhd2Ni4CyOGmujYpqNnp1qfZNhmcj/VOeBAoGBAJgD
stU2c9UVlTIMM7mLG1kVjlzPBtha42ko2j32k3Ol1FPXcdfCVPcaa0ockjnX/rJt
CvP9+9PYs+8iSESF/cFtS/BGMRYH9Qi9NpwHRLMzDIo2GCXRIFpVL+FbCKp5PV/8
xza2uRdVvolG2EYWDjDvym0Zusmx2YtTYI0m8ObXAoGAZ6T8aF6GAZ0s814ZfEcy
zZGrZZQ/MJ7W8ZGdU1/y+204LzfGsW+d+sTPfQPYhn03/qU3SFhP095sYzELeOOZ
3yITOftHEdMP3XffnAudgn3tBHrtu0EsVFL44H7CWe4hx3M49M0lfERD60lPwUG1
8hY5qcthSko1f1WkTgN7Rrs='''s = b64decode(s)print(binascii.hexlify(s))
result:
6573c8d337cce442647a8a11bcdaf744a404a102818100f45ab61bc6106f792458be4395d3ea267eeb704bac08a0299e0980aae4c6e81dd667f0d0c21f2f98eba6fe1bf18c6497b0a8429048bc077008ca1f1a2e9de157a7a031574ae4056b4e44d9e35dfb61b165ef3a0049cc69bc089412fb156d52961ce25d509d8690a5cd3f4829524cf1bbef91f90e727cb78acaa0d42eafefe9730281803d415340235bac7e1983d7533034fed5d0a6ee576803319229e18a2389593fc0131cc953c26d79050b27710310d1ba69c4aec0c866d1630b850d091ba8087a347238165222a8c44961873e6914d576d40f3d222dbd611d3a8930059829626ce119c96f1e8d189021776362e02c8e1a6ba3629a8d9e9d6a7d936199c8ff54e781028181009803b2d53673d51595320c33b98b1b59158e5ccf06d85ae36928da3df69373a5d453d771d7c254f71a6b4a1c9239d7feb26d0af3fdfbd3d8b3ef22484485fdc16d4bf046311607f508bd369c0744b3330c8a361825d1205a552fe15b08aa793d5ffcc736b6b91755be8946d846160e30efca6d19bac9b1d98b53608d26f0e6d702818067a4fc685e86019d2cf35e197c4732cd91ab65943f309ed6f1919d535ff2fb6d382f37c6b16f9dfac4cf7d03d8867d37fea53748584fd3de6c63310b78e399df221339fb4711d30fdd77df9c0b9d827ded047aedbb412c5452f8e07ec259ee21c77338f4cd257c4443eb494fc141b5f21639a9cb614a4a357f55a44e037b46bb
按照证书格式拆分
6573c8d337cce442647a8a11bcdaf744a404a1 028181 00f45ab61bc6106f792458be4395d3ea267eeb704bac08a0299e0980aae4c6e81dd667f0d0c21f2f98eba6fe1bf18c6497b0a8429048bc077008ca1f1a2e9de157a7a031574ae4056b4e44d9e35dfb61b165ef3a0049cc69bc089412fb156d52961ce25d509d8690a5cd3f4829524cf1bbef91f90e727cb78acaa0d42eafefe973 028180 3d415340235bac7e1983d7533034fed5d0a6ee576803319229e18a2389593fc0131cc953c26d79050b27710310d1ba69c4aec0c866d1630b850d091ba8087a347238165222a8c44961873e6914d576d40f3d222dbd611d3a8930059829626ce119c96f1e8d189021776362e02c8e1a6ba3629a8d9e9d6a7d936199c8ff54e781 028181 009803b2d53673d51595320c33b98b1b59158e5ccf06d85ae36928da3df69373a5d453d771d7c254f71a6b4a1c9239d7feb26d0af3fdfbd3d8b3ef22484485fdc16d4bf046311607f508bd369c0744b3330c8a361825d1205a552fe15b08aa793d5ffcc736b6b91755be8946d846160e30efca6d19bac9b1d98b53608d26f0e6d7 028180 67a4fc685e86019d2cf35e197c4732cd91ab65943f309ed6f1919d535ff2fb6d382f37c6b16f9dfac4cf7d03d8867d37fea53748584fd3de6c63310b78e399df221339fb4711d30fdd77df9c0b9d827ded047aedbb412c5452f8e07ec259ee21c77338f4cd257c4443eb494fc141b5f21639a9cb614a4a357f55a44e037b46bb解释一下最后对应的信息 首先在尾部就三个 dp dq inv(q,p)
可能顺序会有些乱,但是注意 dp和dq长度相同 且比inv小1
故提取如下:
q = 0x00f45ab61bc6106f792458be4395d3ea267eeb704bac08a0299e0980aae4c6e81dd667f0d0c21f2f98eba6fe1bf18c6497b0a8429048bc077008ca1f1a2e9de157a7a031574ae4056b4e44d9e35dfb61b165ef3a0049cc69bc089412fb156d52961ce25d509d8690a5cd3f4829524cf1bbef91f90e727cb78acaa0d42eafefe973
inv = 0x009803b2d53673d51595320c33b98b1b59158e5ccf06d85ae36928da3df69373a5d453d771d7c254f71a6b4a1c9239d7feb26d0af3fdfbd3d8b3ef22484485fdc16d4bf046311607f508bd369c0744b3330c8a361825d1205a552fe15b08aa793d5ffcc736b6b91755be8946d846160e30efca6d19bac9b1d98b53608d26f0e6d7
dp = 0x3d415340235bac7e1983d7533034fed5d0a6ee576803319229e18a2389593fc0131cc953c26d79050b27710310d1ba69c4aec0c866d1630b850d091ba8087a347238165222a8c44961873e6914d576d40f3d222dbd611d3a8930059829626ce119c96f1e8d189021776362e02c8e1a6ba3629a8d9e9d6a7d936199c8ff54e781
dq =
0x67a4fc685e86019d2cf35e197c4732cd91ab65943f309ed6f1919d535ff2fb6d382f37c6b16f9dfac4cf7d03d8867d37fea53748584fd3de6c63310b78e399df221339fb4711d30fdd77df9c0b9d827ded047aedbb412c5452f8e07ec259ee21c77338f4cd257c4443eb494fc141b5f21639a9cb614a4a357f55a44e037b46bb
这就导致q泄露,那么通过公钥文件提取n和e 直接解密
用一下我的新工具openssl吧
openssl rsa -pubin -in public.pem -inform PEM -text -noout
Public-Key: (2048 bit)
Modulus:00:eb:8b:b6:a8:e4:8a:c1:17:fa:19:63:eb:ab:d6:57:b9:6a:af:a2:84:ea:da:ec:ff:de:86:e2:a2:25:8c:63:69:76:b4:ba:62:d8:98:22:ab:b1:78:d2:df:50:1c:bb:88:cd:c8:20:53:a6:d1:1f:90:a7:da:0b:21:d4:3b:44:51:06:0b:32:4b:33:6e:9f:3c:6a:44:2a:a4:f1:1a:ee:de:a5:78:8a:a7:4f:c6:78:ac:5a:a3:ea:c4:69:75:84:90:4b:c5:36:17:30:33:58:34:6f:85:8e:28:12:58:b0:72:89:97:f3:85:82:56:1f:01:29:ed:fc:a8:ea:8d:d5:0b:e1:65:50:58:d3:42:68:52:4d:b1:fc:70:45:34:20:3c:56:91:19:21:e4:d2:2a:f1:f4:45:cf:c3:cf:2e:61:2a:81:c1:45:a2:fc:6c:12:d8:8e:1a:8e:d8:f3:5f:02:4b:c7:7b:02:48:a9:1c:aa:b5:75:db:79:da:aa:0e:7e:af:a7:d2:57:e2:55:5c:4b:99:ff:8b:de:64:40:df:7c:25:89:f6:45:2b:a1:4f:19:3e:bf:56:47:a4:48:92:2c:89:b3:73:ef:5a:38:03:cf:b6:c8:a4:64:fb:1a:87:a2:4e:9e:30:db:85:cb:5f:64:64:67:d4:c7:c5:7f:33:9d:53
Exponent: 65537 (0x10001)
即
n = 0x00eb8bb6a8e48ac117fa1963ebabd657b96aafa284eadaecffde86e2a2258c636976b4ba62d89822abb178d2df501cbb88cdc82053a6d11f90a7da0b21d43b4451060b324b336e9f3c6a442aa4f11aeedea5788aa74fc678ac5aa3eac4697584904bc53617303358346f858e281258b0728997f38582561f0129edfca8ea8dd50be1655058d34268524db1fc704534203c56911921e4d22af1f445cfc3cf2e612a81c145a2fc6c12d88e1a8ed8f35f024bc77b0248a91caab575db79daaa0e7eafa7d257e2555c4b99ff8bde6440df7c2589f6452ba14f193ebf5647a448922c89b373ef5a3803cfb6c8a464fb1a87a24e9e30db85cb5f646467d4c7c57f339d53
e = 0x10001
q = 0x00f45ab61bc6106f792458be4395d3ea267eeb704bac08a0299e0980aae4c6e81dd667f0d0c21f2f98eba6fe1bf18c6497b0a8429048bc077008ca1f1a2e9de157a7a031574ae4056b4e44d9e35dfb61b165ef3a0049cc69bc089412fb156d52961ce25d509d8690a5cd3f4829524cf1bbef91f90e727cb78acaa0d42eafefe973
exp:
n = 0x00eb8bb6a8e48ac117fa1963ebabd657b96aafa284eadaecffde86e2a2258c636976b4ba62d89822abb178d2df501cbb88cdc82053a6d11f90a7da0b21d43b4451060b324b336e9f3c6a442aa4f11aeedea5788aa74fc678ac5aa3eac4697584904bc53617303358346f858e281258b0728997f38582561f0129edfca8ea8dd50be1655058d34268524db1fc704534203c56911921e4d22af1f445cfc3cf2e612a81c145a2fc6c12d88e1a8ed8f35f024bc77b0248a91caab575db79daaa0e7eafa7d257e2555c4b99ff8bde6440df7c2589f6452ba14f193ebf5647a448922c89b373ef5a3803cfb6c8a464fb1a87a24e9e30db85cb5f646467d4c7c57f339d53
e = 0x10001
q = 0x00f45ab61bc6106f792458be4395d3ea267eeb704bac08a0299e0980aae4c6e81dd667f0d0c21f2f98eba6fe1bf18c6497b0a8429048bc077008ca1f1a2e9de157a7a031574ae4056b4e44d9e35dfb61b165ef3a0049cc69bc089412fb156d52961ce25d509d8690a5cd3f4829524cf1bbef91f90e727cb78acaa0d42eafefe973
p = n // q
phi = (p - 1) * (q - 1)
import gmpy2
from Crypto.Util.number import *
d = gmpy2.invert(e, phi)
c = open('flag.txt.enc','rb').read() #二进制读取
c = bytes_to_long(c)
print(long_to_bytes(pow(c,d,n)))
flag : gigem{Q_Fr0M_Pr1V473_K3Y_89JD54}
Truncated 2
题目描述
It seems even less was able to be retrieved this time. Decrypt the flag.txt.enc file.
附件
private.pem
WXH2tecCgYBIlOn6LCaw4cYxztL4a+AgeoJ1HXB7AYg5Vl6T9VHfWW6dFvBVmaK/
sLuzAAZBOfOD3oXHk+BY2izOQamgOY5AvgW7m4JwP+gEFk9f9NdmI9DkxyD9cFzm
76zpeUiaizor1mMAd2mcCqjaYlDB3ohA0+Wvw024ZeBlDOCPgotJrQKBgFTU0ZgY
cNeZM05a5RdFJtKXnhTG7MdNe1lgD799tMBgSBw9OMg6pASOTGrUg6QW1DrsxY23
/ouePRFBh1OMArIskZf+Ov0jqD9umsM/q1XIR3ax3iOmBX6RxH42qyrHYArbv+tB
WdiwnYGJj5oE5HtnnL5pDa9qYFUfK4InhjN3AoGAZ2q2zPPhW9v75hq8fwVvLGjP
yDT4gGIz168dnCBLLMHsNv8y0twKQMY8UnqKBBIIkaC+j6zdCM+9CU3SEGC/TwQc
5iTOHmknFfuvRYN6WKOXbTQZJIx2aDHaRz4MZlpHOVFeHrmY9/s+y24U2nOG9kAC
zBzyXKI5PxT40b/mIGs=
-----END PRIVATE KEY-----
public.pem
-----BEGIN PUBLIC KEY-----
MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAy+KEz83nu2HZ1fy9jec/
twHw1bkdZJStKl9J2wIo21gvJmcr+VyUcozF8mJgZKTVBvu57GTd6PhcCjyqnbH3
KB63Nji2imT8DVzHaNVTBHu1c3jm/9dNBe6qp3SxSGozO00pE/27VOrEIRwM+595
kHIO7YKWfPbdXuSp5XyVAdX9+I1gtGNYLc+yjO5h5bwHm95Le0sW8/T/Sl2i/M5d
wlYwpidyBhIJ7WPKBcgiAe0etC9XKoA5JPmtv+U3BQ5k/75hGq6pL0vxYIS4WlU8
fij2aD3QooEQJyV+8dleXQ2q0MBKRPcQGLzuM6hFVc8DesPm3g84FiNeR+jdtNNQ
iwIDAQAB
-----END PUBLIC KEY-----
解题:
先用openssl把公钥拆了 看看大小
Public-Key: (2048 bit)
Modulus:00:cb:e2:84:cf:cd:e7:bb:61:d9:d5:fc:bd:8d:e7:3f:b7:01:f0:d5:b9:1d:64:94:ad:2a:5f:49:db:02:28:db:58:2f:26:67:2b:f9:5c:94:72:8c:c5:f2:62:60:64:a4:d5:06:fb:b9:ec:64:dd:e8:f8:5c:0a:3c:aa:9d:b1:f7:28:1e:b7:36:38:b6:8a:64:fc:0d:5c:c7:68:d5:53:04:7b:b5:73:78:e6:ff:d7:4d:05:ee:aa:a7:74:b1:48:6a:33:3b:4d:29:13:fd:bb:54:ea:c4:21:1c:0c:fb:9f:79:90:72:0e:ed:82:96:7c:f6:dd:5e:e4:a9:e5:7c:95:01:d5:fd:f8:8d:60:b4:63:58:2d:cf:b2:8c:ee:61:e5:bc:07:9b:de:4b:7b:4b:16:f3:f4:ff:4a:5d:a2:fc:ce:5d:c2:56:30:a6:27:72:06:12:09:ed:63:ca:05:c8:22:01:ed:1e:b4:2f:57:2a:80:39:24:f9:ad:bf:e5:37:05:0e:64:ff:be:61:1a:ae:a9:2f:4b:f1:60:84:b8:5a:55:3c:7e:28:f6:68:3d:d0:a2:81:10:27:25:7e:f1:d9:5e:5d:0d:aa:d0:c0:4a:44:f7:10:18:bc:ee:33:a8:45:55:cf:03:7a:c3:e6:de:0f:38:16:23:5e:47:e8:dd:b4:d3:50:8b
Exponent: 65537 (0x10001)
再用脚本把私钥文件转化成十六进制
5971f6b5e7
028180 dp
4894e9fa2c26b0e1c631ced2f86be0207a82751d707b018839565e93f551df596e9d16f05599a2bfb0bbb300064139f383de85c793e058da2cce41a9a0398e40be05bb9b82703fe804164f5ff4d76623d0e4c720fd705ce6eface979489a8b3a2bd6630077699c0aa8da6250c1de8840d3e5afc34db865e0650ce08f828b49ad
028180 dq
54d4d1981870d799334e5ae5174526d2979e14c6ecc74d7b59600fbf7db4c060481c3d38c83aa4048e4c6ad483a416d43aecc58db7fe8b9e3d114187538c02b22c9197fe3afd23a83f6e9ac33fab55c84776b1de23a6057e91c47e36ab2ac7600adbbfeb4159d8b09d81898f9a04e47b679cbe690daf6a60551f2b8227863377
028180 ?打个问号
676ab6ccf3e15bdbfbe61abc7f056f2c68cfc834f8806233d7af1d9c204b2cc1ec36ff32d2dc0a40c63c527a8a04120891a0be8facdd08cfbd094dd21060bf4f041ce624ce1e692715fbaf45837a58a3976d3419248c766831da473e0c665a4739515e1eb998f7fb3ecb6e14da7386f64002cc1cf25ca2393f14f8d1bfe6206b
那么现在就n和e和dp进行求解
在鸡块哥哥这边看到一个比较巧妙的解法

注意这里面的所有运算都是同余,设t的值 和 g的值,经过推导,计算出p的值
因为g - 2 = k * p 且 n = p * q 故两数有公因子
但是现在不清楚的是,在推导g的时候,为什么可以直接去掉edp
教你怎么去:
2 e d p ≡ 2 ( m o d p ) 推导如下: d p = d + k ( p − 1 ) 故: 2 e d p = 2 e [ d + k ( p − 1 ) ] = 2 e d + e k ( p − 1 ) 对于 2 p − 1 m o d p ∵ ( 2 , p ) = 1 根据欧拉定理 2 p − 1 ≡ 1 m o d p ∴ 2 e d + e k ( p − 1 ) ≡ 2 e d m o d p 根据循环节 2 e d ≡ 2 e d m o d ( p − 1 ) m o d p ∵ e d ≡ 1 m o d ϕ ( n ) e d ≡ 1 m o d ( p − 1 ) ( q − 1 ) 根据同余的性质,模模数的因子其同余性质不改变 ∴ e d ≡ 1 m o d ( p − 1 ) ∴ 根据循环节 2 e d ≡ 2 e d m o d ( p − 1 ) ≡ 2 m o d p 推导毕 2^{edp}\equiv2~(mod~p)推导如下:\\ dp=d+k(p-1)\\ 故:2^{edp}=2^{e[d+k(p-1)]}=2^{ed+ek(p-1)}\\ 对于2^{p-1}mod~p \\ \because(2,p)=1 根据欧拉定理 2^{p-1}\equiv1~mod~p\\ \therefore 2^{ed+ek(p-1)} \equiv2^{ed}~mod~p \\根据循环节 2^{ed} \equiv2^{ed~mod~(p-1)}~mod~p \\\because ed \equiv1~mod~\phi(n)\\ ed \equiv1~mod~(p-1)(q-1)\\ 根据同余的性质,模 模数的因子 其同余性质不改变\\ \therefore ed \equiv1~mod~(p-1) \\\therefore 根据循环节 2^{ed} \equiv2^{ed~mod~(p-1)} \equiv 2~mod~p~~~~推导毕 2edp≡2 (mod p)推导如下:dp=d+k(p−1)故:2edp=2e[d+k(p−1)]=2ed+ek(p−1)对于2p−1mod p∵(2,p)=1根据欧拉定理2p−1≡1 mod p∴2ed+ek(p−1)≡2ed mod p根据循环节2ed≡2ed mod (p−1) mod p∵ed≡1 mod ϕ(n)ed≡1 mod (p−1)(q−1)根据同余的性质,模模数的因子其同余性质不改变∴ed≡1 mod (p−1)∴根据循环节2ed≡2ed mod (p−1)≡2 mod p 推导毕
exp:
n = 0x00cbe284cfcde7bb61d9d5fcbd8de73fb701f0d5b91d6494ad2a5f49db0228db582f26672bf95c94728cc5f2626064a4d506fbb9ec64dde8f85c0a3caa9db1f7281eb73638b68a64fc0d5cc768d553047bb57378e6ffd74d05eeaaa774b1486a333b4d2913fdbb54eac4211c0cfb9f7990720eed82967cf6dd5ee4a9e57c9501d5fdf88d60b463582dcfb28cee61e5bc079bde4b7b4b16f3f4ff4a5da2fcce5dc25630a62772061209ed63ca05c82201ed1eb42f572a803924f9adbfe537050e64ffbe611aaea92f4bf16084b85a553c7e28f6683dd0a2811027257ef1d95e5d0daad0c04a44f71018bcee33a84555cf037ac3e6de0f3816235e47e8ddb4d3508b
e = 0x10001#==dp大法==========================
dp = 0x4894e9fa2c26b0e1c631ced2f86be0207a82751d707b018839565e93f551df596e9d16f05599a2bfb0bbb300064139f383de85c793e058da2cce41a9a0398e40be05bb9b82703fe804164f5ff4d76623d0e4c720fd705ce6eface979489a8b3a2bd6630077699c0aa8da6250c1de8840d3e5afc34db865e0650ce08f828b49ad
t = pow(2,e,n)
g = pow(t,dp,n)
import gmpy2
p = gmpy2.gcd(g - 2, n)
q = n // p#==常规RSA===================================
phi = (p - 1) * (q - 1)
import gmpy2
from Crypto.Util.number import *
d = gmpy2.invert(e, phi)
c = open('flag.txt.enc','rb').read() #二进制读取
c = bytes_to_long(c)
print(long_to_bytes(pow(c,d,n)))
flag : gigem{DP_DQ_r54_7rUNC473D_SDA79}
Jumbled
题目描述
The RSA public and private keys are provided. However, the private key seems to be jumbled in a block size of 10 hex characters. Can you get the flag?
附件
public.pem
-----BEGIN PUBLIC KEY-----
MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAqmTYhYT7+NBzZDrsfKD4
4K+9rtLcZLT+VaWHYvn8Bp9X/fg7TmK5l5D6MsF89rZ8taEGFJPy+kx+qUqOO95G
QhM2SXAwn0D1TJKdaSZunG06pcQ3b+pb5GDYYp43P7agUsgHSCw2OFCtU/Ms53Ew
i2j51dEv+8KbuqIp2IOGzLy3Mzx4r1TjTIm18DnpVVeoy8sNtWbVdnCCtIY6LnPP
smaOJ1+jWrWgv9DndpZIeDOuozd1bKltLBeIK2kfFnoxomTgW+SASL4rn/ojqNc0
6CZ5L+KnDCBybhG3sgTimzw0QMrS5G35kFv2l3M7/8WHOiXWpSSZKmKq1Tsbev+r
lwIDAQAB
-----END PUBLIC KEY-----
private
49 45 4e 42 47 2d 2d 2d 2d 2d
20 54 4b 41 45 49 50 56 20 52
0a 2d 4d 2d 0d 2d 59 2d 45 2d
44 42 41 49 41 76 49 41 49 45
47 6b 39 68 69 6b 42 71 4e 67
41 46 53 45 41 41 30 51 77 42
...
解题:
题目中说,我们的私钥证书,每十个一组 ,然后在一组中跳跃,就表示10个区间内会出现乱序。
根据基础知识中我们私钥证书的标准格式
-----BEGIN RSA PRIVATE KEY----- ... -----END RSA PRIVATE KEY-----可以发现开头和结尾有固定的值的,所以转化为16进制
s = "-----BEGIN RSA PRIVATE KEY-----" print(s.encode().hex())2d 2d 2d 2d 2d 42 45 47 49 4e 20 50 52 49 56 41 54 45 20 4b 45 59 2d 2d 2d 2d 2d拿过跳跃后的前几个找规律
jumped: 49 45 4e 42 47 2d 2d 2d 2d 2d standa: 2d 2d 2d 2d 2d 42 45 47 49 4e jumped: 20 54 4b 41 45 49 50 56 20 52 standa: 20 50 52 49 56 41 54 45 20 4b可以发现前后五个互换 采用数组下标表示正确数据
9,7,10,6,8,4,2,5,1,3
exp:
with open('private', 'r') as file:jump_hex = file.read()jump = list(jump_hex.split(' '))
print(jump)#10个一分组
BLOCK_SIZE = 10
ori = []
for i in range(len(jump) // BLOCK_SIZE):ori.append(jump[BLOCK_SIZE * i : BLOCK_SIZE * i + BLOCK_SIZE])
print(ori)#组内恢复顺序
for i in ori:temp = [i[8],i[6],i[9],i[5],i[7],i[3],i[1],i[4],i[0],i[2]]for j in temp:print(chr(int(j,16)),end="")
-----BEGIN PRIVATE KEY-----
MIIEvAIBADANBgkqhkiG9w0BAQEFAASCBKYwggSiAgEAAoIBAQCqZNiFhPv40HNk
Oux8oPjgr72u0txktP5VpYdi+fwGn1f9+DtOYrmXkPoywXz2tny1oQYUk/L6TH6p
So473kZCEzZJcDCfQPVMkp1pJm6cbTqlxDdv6lvkYNhinjc/tqBSyAdILDY4UK1T
8yzncTCLaPnV0S/7wpu6oinYg4bMvLczPHivVONMibXwOelVV6jLyw21ZtV2cIK0
hjouc8+yZo4nX6NataC/0Od2lkh4M66jN3VsqW0sF4graR8WejGiZOBb5IBIviuf
+iOo1zToJnkv4qcMIHJuEbeyBOKbPDRAytLkbfmQW/aXczv/xYc6JdalJJkqYqrV
Oxt6/6uXAgMBAAECggEAAU8gCLqSUwGK+Wioe3ajItrGysqM7eskDxVj+mMwR/6+
ZtGa5wnEIkF3Yp9w7dZOE/kmOk8+rSScToGnoRcelBBguOS3Qun1WH7B3dZxQBto
uXBN+rqitRj3YJ6VjxRAnBI0WB4a1ojsI/p4zFhmxpNqY/Wk+DqxBpiLWMH97aG8
UcQhR2CtLP09O/EV8FDCI1NCthE0RYX9vkWCsDEbN9QEthxq8lgQyJKUKaK3Yl4q
v2baj4PKgsAJHtx99KJAYkD4Xp0kYtsWK0TOjEDuZPSchB11QJxiquhZRG9z+geo
TU4eEGPXqj7Q3+9dKHjIqIMXFE0/FKJT+CXnZU235QKBgQDFmc+tjBdUwLfb/cjS
M3Q8od0FKRV4IE4dBUlyRPNjhFLzUvzuSchRDFARcNUz7MAf+EBAMcMP/9pjKXyP
KcXCaSqmKEIBhjNNUR/BisabNlokxBu8CosuE9lgX+f8mbp5cKD3Fnjqh81QWKm6
LtgNdHVHj7nz2IgmIa2hXcgpgwKBgQDcwJnEhieqri7IUFc4fEpnzK62xtTg6C1y
hCUoqtBLKiSeEZZI46tnRgEZBxY75/Yq+nwvMhPbPsX7HRGEa7WyVcY9dr40h1Ks
TNTiNrwfue4n0TlidGuv/i8Zp6xS0idQD0BL6XXrpvI+JDoUVKSz1pidoRJ9uNv9
uPSrErxdXQKBgBxAY3rynptVenQPktjK1oGcutb0CsfEBqcLjHaz+QBveNSlNthy
4BsGYaQ8t57W6JkpizYiZzswX27yDYcCd+3Vz202MEm7gDY7tQic6MxkNvsutrBp
6YBLAjdPPwHUkN6wBbOOGPefNvGX25xs+iLiVapHmFSOzth01DhQCkA1AoGAbib1
E6lVlceAtJfSTe9HOXBbJf0lMGzqcKAb4qUJdtg6mV1xPkHMv6Wg2po8r/vZTCzd
VreITPiP1fP1T7xnV+uRFg5wbsmvqSZVe+OQD8y5V8kA923cZl9RpV2TkWgoEbzq
enauTr5pVjTBfm+WF97XHKDJF07tBzgJbmvU7kkCgYAz+FdbBcZEj9KPt2J1O8rl
hL7J6eUuip1JSkLclg27yetxFlAPqLSwv5GTgdRR6/+tT/ilt+JkmYPTAbI5p3bD
wFbwjgYhiw+DL/KXIEbRs5sqqhhAzgB+6zFMTKR8yPtyw+PC6W7CnYVrvN2a3eVe
palIDTkjSFadyj7owR7OtQ==
-----END PRIVATE KEY-----
这种完整的私钥文件得到后,就不要自己手撕了,上工具就好
openssl rsa -in private.pem -text -noout
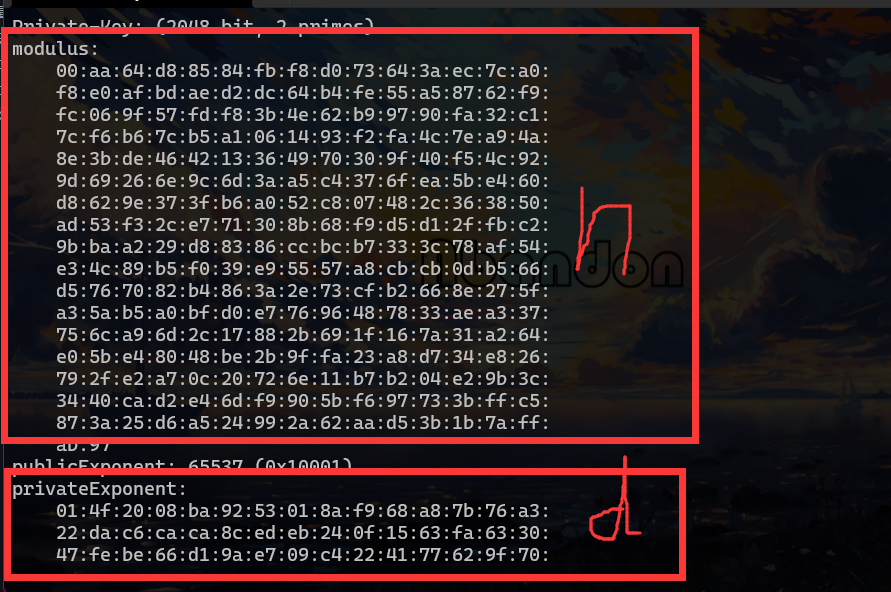
好像附件还给了public 但是显然没有用了
flag: gigem{jumbl3d_r54_pr1v473_k3y_z93kd74lx}